How journalists can protect their sources from the snoopers
Roy GreensladeImage may be NSFW.
Clik here to view.
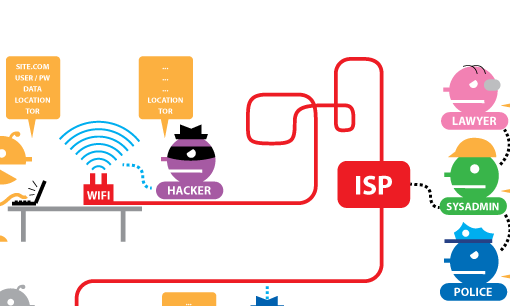
The Electronic Frontier Foundation's graphic to show what's visible to eavesdroppers (see link below) Photograph: Public domain
Wednesday 26 November 2014 13.30 GMT
Is what you write on your computer safe? Who can look at what you’re writing? And how does the surveillance system work?
Paul Bradshaw comes up with some answers in a posting on his online journalism blog, The government wants to know where you were online, when. Why journalists should be cautious.
He points to a very interesting graphic, produced by the Electronic Frontier Foundation, just part of which is reproduced above.
It shows what information can be gathered by hackers, internet service providers (ISPs), police and lawyers when someone browses the web without HTTPS or Tor. It also shows what information is left after using either, or both, tools.
As Bradshaw notes, home secretary Theresa May wants to be able to connect IP addresses (which identify machines) with their users.
Her counter terrorism bill includes a clause that will require ISPs to retain data on internet protocol addresses to allow individual users to be identified. In other words, it will allow the police to identify whether the user was in a particular place (a website) at a particular time.
Her justification for the snooping, as Bradshaw also notes, is to identify terrorists and paedophiles. But what’s to stop the police from identifying journalists’ sources, as they have done in their use (misuse?) of the Regulation of Investigatory Powers Act (Ripa).
We have heard that police have been gathering detailed information about at least six journalists, ranging from their sexual orientation to things that they have tweeted about.
We also know from today’s revelation in the Times (see here and here) that the police were willing to hang on to phone records sent to them in error by a mobile phone company, Vodafone.
So, as Bradshaw writes, “it’s safe to assume that, if this law is passed, yet more information about your virtual whereabouts and those of your sources will become fair game. And if you and a source are in the same virtual place at the same time, you have a problem.” Exactly.
23
It would have been great if this article actually did what it promised in the headline and provided some practical advice on how journalists can protect their sources from snoopers.
Reply
Report
- It does, it's the bit where it saysHTTPS or TorThe linked-to diagram show the effect of using HTTPS on both snoopers and admins as well as traditional evesdroppers.Head to the interactive diagram The Government wants to know where you were online, when. Why journalists should be cautious | Online Journalism Blog and click on the "HTTPS" and "TOR" buttons.
